How a digital chain of custody improves data protection and AI outcomes
If you’ve ever watched crime shows like Law and Order, or Bones, you’ve probably heard about the chain of custody. It’s a forensic technique that documents a piece of evidence from the time it was obtained to the time it is disposed of. It provides a clear record of who had access to it, where it was transported to and when, and any changes in status.
Why is the chain of custody important?
Any break or discrepancy in the chain of custody puts the integrity of the evidence in jeopardy. Its authenticity can then be questioned in court. That’s why law enforcement agencies don’t let just anyone remove a piece of evidence from a crime scene or trust that it would be returned tamper-free to a designated storage area.
What does this have to do with your business data?
It’s all about ensuring data integrity. Nothing is more important in today’s data-driven world. If you can’t trust your digital data, you can’t trust your decisions. And you’re more likely to make poor ones.
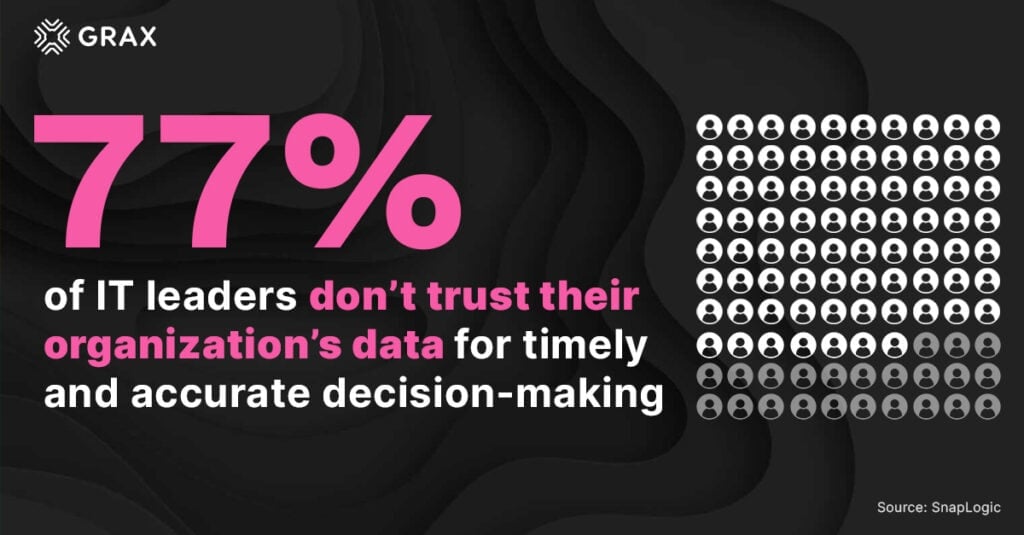
The harsh reality is 77% of IT leaders don’t trust their organization’s data for timely and accurate decision-making. And two-thirds of all senior business executives admit to having some reservations or actively mistrusting their data and analytics.
They aren’t wrong to feel this way. With so many people having access to an organization’s critical data systems these days – and cybercriminals using sophisticated methods to infiltrate and alter or extract data – it’s getting harder and harder to ensure data authenticity and security. But doing so is more important than ever in our data-driven world.
One increasingly popular and effective way to accomplish this is with a digital chain of custody for data.
Digital Chain of Custody Definition
A digital chain of custody is the process of tracking and documenting every interaction with data within an organization. This includes who accessed the data, when it was accessed, where it was accessed from, and any changes made. Much like the physical chain of custody used in legal contexts, the digital chain of custody ensures data handling is transparent and traceable, safeguarding it from tampering and misuse.
The Role of Digital Chain of Custody in Data Protection
Implementing a digital chain of custody transforms data protection from reactive to proactive. Here are 5 ways this benefits organizations:
Audit Trails
A digital chain of custody creates a clear and detailed audit trail for every piece of data over time. These audit trails are essential for monitoring historical data usage, detecting any unauthorized access or modifications, and enabling immediate remedial action.
Access Controls
Implementing a digital chain of custody typically involves strict access controls to ensure that only authorized personnel can interact with sensitive data. These controls are enforced through authentication and authorization mechanisms that restrict data access based on user roles and permissions.
Incident Response and Forensics
In the event of a data breach or other security incident, a well-maintained digital chain of custody is invaluable for forensic analysis. Forensic investigators can quickly trace back through the data’s history to understand the scope of the breach, identify how the breach occurred, and which data was affected. This accelerates the incident response and recovery process while minimizing the impact on your organization. Using digital forensic tools also helps in the prosecution of perpetrators by providing irrefutable digital evidence of the crime.
Compliance and Regulation Adherence
Many industries are subject to regulations that require tracking data for compliance purposes. A digital chain of custody helps organizations comply with laws such as GDPR, HIPAA, or Sarbanes-Oxley by providing the necessary documentation to prove that data has been handled properly throughout its lifecycle.
Long-term Data Management
For industries that require long-term data retention (like legal, medical, or research fields), a digital chain of custody ensures that data remains accessible, traceable, and unchanged over time. This is essential for archival purposes where data authenticity and integrity must be maintained for many years.
Chain of Custody Impact on Decision-Making, Analytics and AI
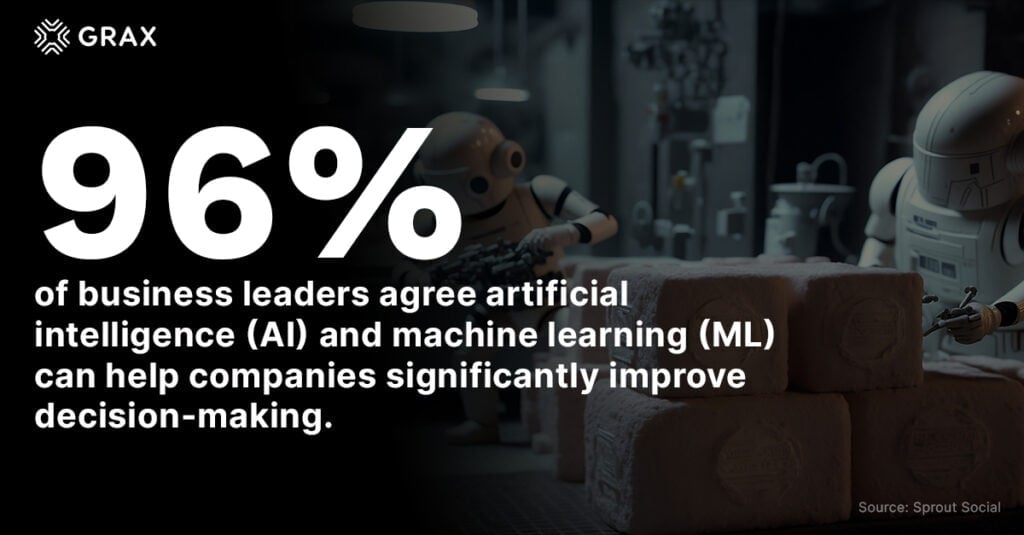
The potential for analytics and AI to transform business is undeniable. 96% of business leaders agree AI and machine learning (ML) can help companies significantly improve decision-making. That’s why 83.9% planned to increase their investments in data, analytics, and AI.
But potential can’t be realized with questionable data. In fact, using data you’re not confident about could do more harm than good.
ML and AI models are only as good as the data they are trained on. They often require vast amounts of data to learn from. If this data is corrupted or altered maliciously, it can lead to biased or incorrect model outcomes.
A digital chain of custody helps ensure that all data used in training machine learning models has been accurately logged and remains unaltered from its original state. This preserves the integrity of the training process and the reliability of the models.
By helping secure the infrastructure itself against potential threats, it also reduces the risk of errors or manipulations that could lead to faulty decision-making and catastrophic actions and outcomes.
Secure your data integrity, streamline compliance, and boost your strategic decisions!
Read our e-book to learn how.
5 Best Practices for Maintaining a Digital Chain of Custody
Own your data in your own cloud
Ownership is essential for maintaining a Digital Chain of Custody. It means you continually possess and are fully responsible for protecting your company’s data. You can’t do this if it’s not always in your possession.
GRAX’s Bring Your Own Cloud (BYOC) data protection model gives you control of your data because it never touches a system that you don’t own. With GRAX, all your historical Salesforce data is replicated directly into your own AWS or GCP cloud. It’s never stored in GRAX’s infrastructure.
Implement comprehensive access controls
Use secure access protocols and robust authentication mechanisms to ensure only authorized personnel can access appropriate data.
Conduct regular audits and reviews
Adhere to a schedule for auditing and reviewing access logs and modifications. This will help ensure adherence to data handling policies.
Use encryption
Protect data at rest and in transit to maintain its confidentiality and integrity. Consider technologies such as cryptographic hashing for securing each transaction in the data’s lifecycle. This is particularly important for critical data that impacts business decisions, legal matters, or customer trust.
Continuous monitoring
Deploy tools that provide real-time monitoring and alerts for unauthorized data interactions so you can quickly respond to potential breaches.
Maintaining a digital chain of custody for data is critical for business success. Investing in robust practices and technologies now can prepare you for today’s data-driven reality, tomorrow’s challenges, and a whole new world of opportunities.
Are you breaking your data’s chain of custody?
It’s time to fix your data integrity issues.